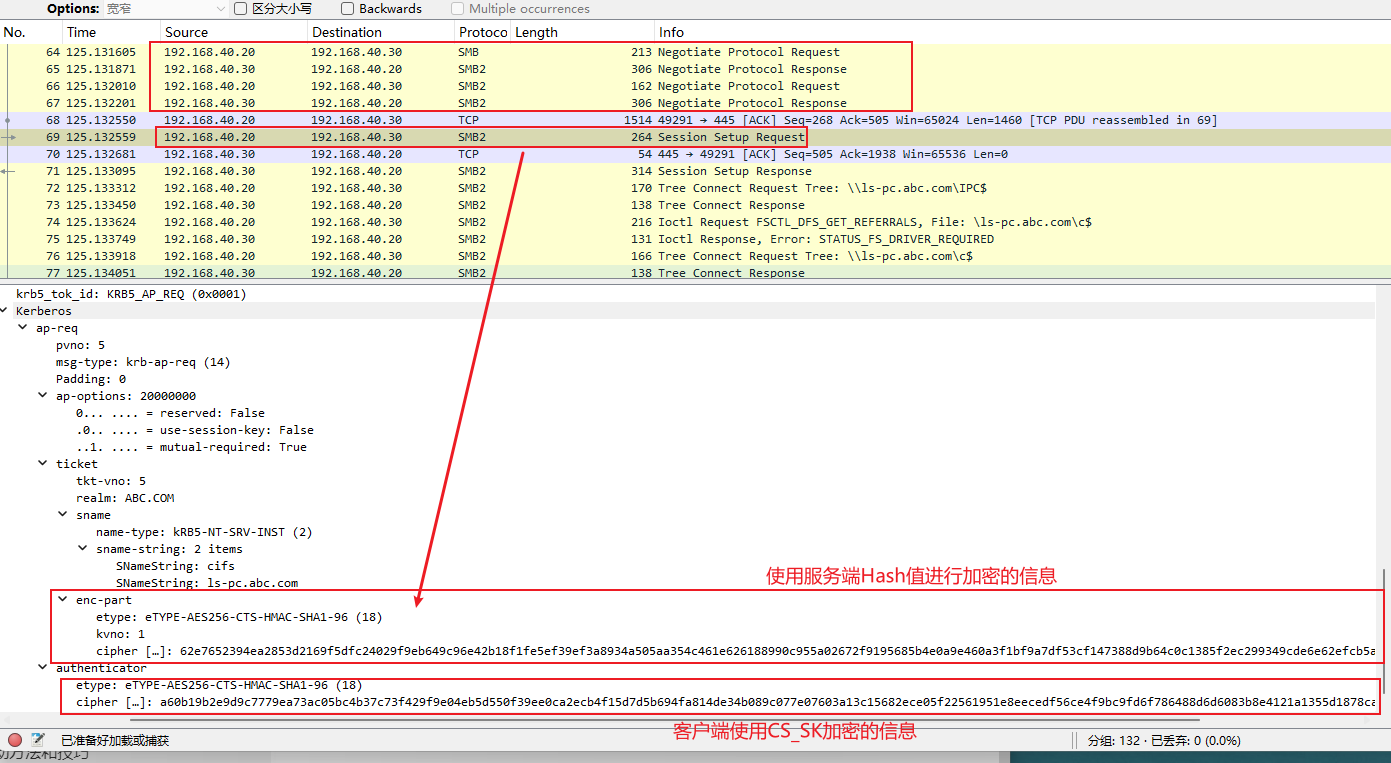
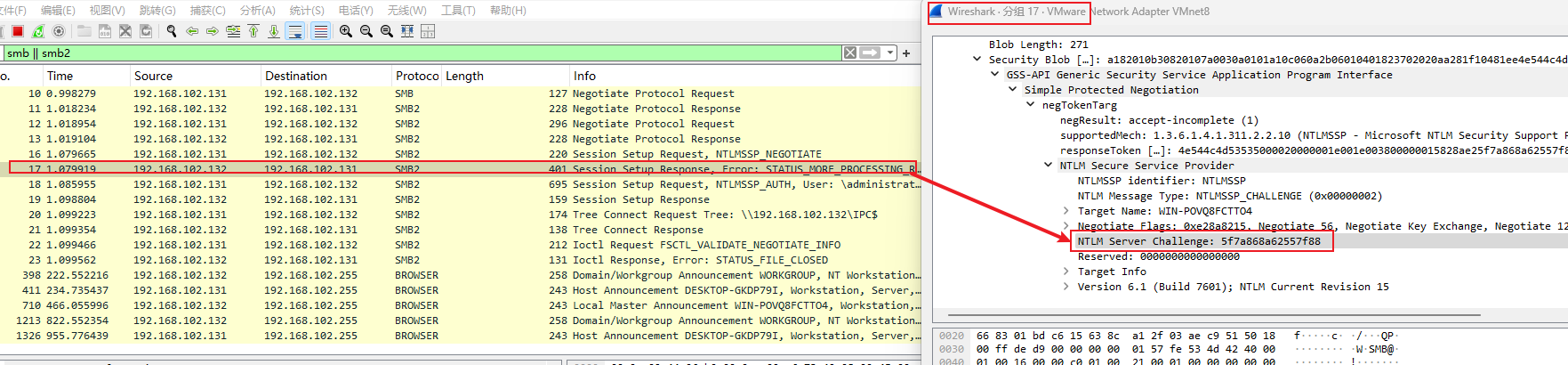
测试环境
测试通过Windows10来使用net use 来对Windows7进行认证。
Challenge
Challenge的值由NTML认证抓包分析可得到该值是认证的服务端发送给客户端的随机字符,如果8位对应的是NTLM v1协议,16对应的NTLM v2协议。
Response
Response是通过客户端发送给服务端的认证信息。
Response的构成方式:
Response = NTProofStr + blob,两部分拼接起来的。
NTProofStr:NTLM-v2-Hash值和Challenge+blob进行HMAC-MD5加密。
NTLM-v2-hash:大写的用户名+域名进行16进制转码,然后编码成Unicode格式,然后用对应用户密码的NTLM-Hash值进行HMAC-MD5加密。
blob是由时间,目标信息,随机填充字符等生成。
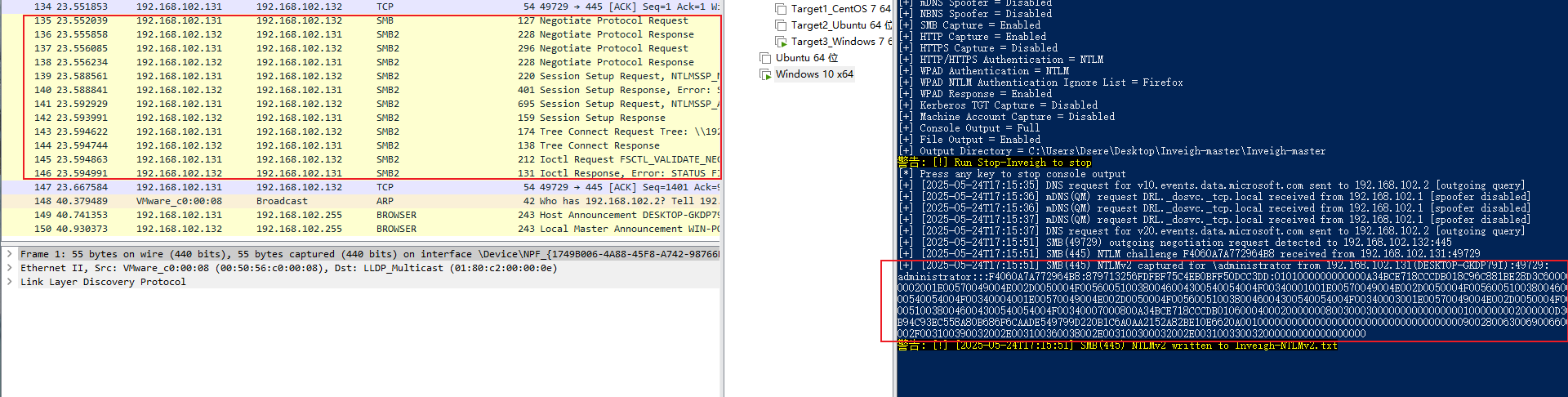
使用工具进行获取NTLM-v2-Hash的值
在当前 PowerShell 会话中允许执行未签名的本地脚本:
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
导入模块
Import-Module .\Inveigh.ps1
开启获取:
Invoke-Inveigh -ConsoleOut Y -FileOutput y同时开启Inveigh还WireShark
Inveigh来获取NTLM-v2-Hash的值,还有Challenge。
WireShark来获取Respnose的值,来对手动生成的值进行对比。
WireShark中获取的值
这里从WireShark获取到的response的值:
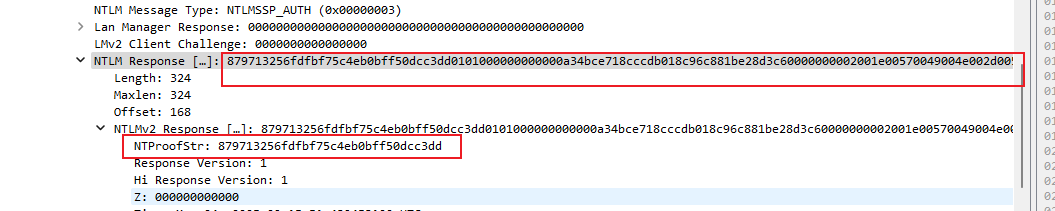
879713256fdfbf75c4eb0bff50dcc3dd0101000000000000a34bce718cccdb018c96c881be28d3c60000000002001e00570049004e002d0050004f0056005100380046004300540054004f00340001001e00570049004e002d0050004f0056005100380046004300540054004f00340004001e00570049004e002d0050004f0056005100380046004300540054004f00340003001e00570049004e002d0050004f0056005100380046004300540054004f00340007000800a34bce718cccdb01060004000200000008003000300000000000000001000000002000000d304db94c93ec558a80b686f6caade549799d220b1c6a0aa2152a82be10e6620a001000000000000000000000000000000000000900280063006900660073002f003100390032002e003100360038002e003100300032002e003100330032000000000000000000
Challenge的值:
f4060a7a772964b8NTProofStr的值:
879713256fdfbf75c4eb0bff50dcc3dd利用Inveigh工具获取的值
该工具在Windows10上进行运行。
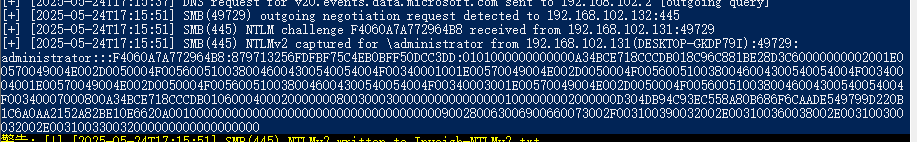
Challenge的值:
F4060A7A772964B8NTLMv2的值:格式:username::domain:challenge:NTProofStr:blob
administrator:::F4060A7A772964B8:879713256FDFBF75C4EB0BFF50DCC3DD:0101000000000000A34BCE718CCCDB018C96C881BE28D3C60000000002001E00570049004E002D0050004F0056005100380046004300540054004F00340001001E00570049004E002D0050004F0056005100380046004300540054004F00340004001E00570049004E002D0050004F0056005100380046004300540054004F00340003001E00570049004E002D0050004F0056005100380046004300540054004F00340007000800A34BCE718CCCDB01060004000200000008003000300000000000000001000000002000000D304DB94C93EC558A80B686F6CAADE549799D220B1C6A0AA2152A82BE10E6620A001000000000000000000000000000000000000900280063006900660073002F003100390032002E003100360038002E003100300032002E003100330032000000000000000000domain为空
challenge=F4060A7A772964B8
NTProofStr=879713256FDFBF75C4EB0BFF50DCC3DD
剩下的数据为blob
计算Response
计算NTLM-v2-Hash的值
1、首先将administrator转换为大写:ADMINISTRATOR
2、这里获取的域名为空所以大写用户名+域名:ADMINISTRATOR
3、将用户名+域名字符串转位16进制:41444d494e4953545241544f52
4、将16进制转为Unicode:410044004d0049004e004900530054005200410054004f005200
5、利用该用户的NTLM-Hash值作为key来加密上述Unicode:
该用户的NTLM-Hash:570a9a65db8fba761c1008a51d4c95ab
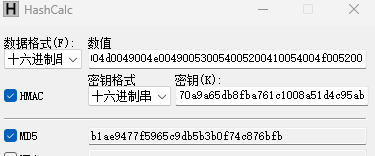
加密后的到ntlm-v2-hash的值:b1ae9477f5965c9db5b3b0f74c876bfb
计算NTProofStr的值
NTProofStr的值是通过NTLM-v2-Hash值作为key来对Challenge+blob进行HMAC-MD5加密。
通过上述工具可获取:
Challenge+blob=F4060A7A772964B80101000000000000A34BCE718CCCDB018C96C881BE28D3C60000000002001E00570049004E002D0050004F0056005100380046004300540054004F00340001001E00570049004E002D0050004F0056005100380046004300540054004F00340004001E00570049004E002D0050004F0056005100380046004300540054004F00340003001E00570049004E002D0050004F0056005100380046004300540054004F00340007000800A34BCE718CCCDB01060004000200000008003000300000000000000001000000002000000D304DB94C93EC558A80B686F6CAADE549799D220B1C6A0AA2152A82BE10E6620A001000000000000000000000000000000000000900280063006900660073002F003100390032002E003100360038002E003100300032002E003100330032000000000000000000
NTLM-v2-hash的值已经计算出来了:b1ae9477f5965c9db5b3b0f74c876bfb
然后利用NTLM-v2-hash作为key来对Challenge+blob进行HMAC-MD5加密:
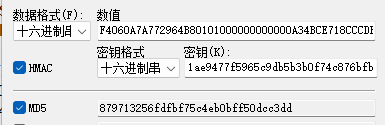
NTProofStr=879713256fdfbf75c4eb0bff50dcc3dd,与工具中获取的值进行对比发现计算出来的一致。
Response的值
Response的值为:Response= NTProofStr+blob
则可通过计算出来的值来获取到Response:
Response:
879713256fdfbf75c4eb0bff50dcc3dd0101000000000000A34BCE718CCCDB018C96C881BE28D3C60000000002001E00570049004E002D0050004F0056005100380046004300540054004F00340001001E00570049004E002D0050004F0056005100380046004300540054004F00340004001E00570049004E002D0050004F0056005100380046004300540054004F00340003001E00570049004E002D0050004F0056005100380046004300540054004F00340007000800A34BCE718CCCDB01060004000200000008003000300000000000000001000000002000000D304DB94C93EC558A80B686F6CAADE549799D220B1C6A0AA2152A82BE10E6620A001000000000000000000000000000000000000900280063006900660073002F003100390032002E003100360038002E003100300032002E003100330032000000000000000000
计算出来的Response的值跟WireShark中抓包获取的Response的值进行对比,可发现两者值除大小写外均一致。